Writing Security Tools and Exploits
(税込) 送料込み
商品の説明
新品のまま本棚にて保管してましたが、保管中にできた折れ目などが端にあります。
当時49.95ドルで購入したものです。
#セキュリティ
#ハッキング商品の情報
| カテゴリー | 本・雑誌・漫画 > 本 > コンピュータ・IT |
|---|---|
| 商品の状態 | 新品、未使用 |

Writing Security Tools and Exploits

Writing Security Tools and Exploits

Writing Security Tools and Exploits

Writing Security Tools and Exploits

Writing Security Tools and Exploits 1, Foster, James C, eBook

Network Security Tools: Writing, Hacking, and Modifying Security Tools

Amazon.com: Writing Security Tools and Exploits: 9781597499972
Network Security Tools [Book]

Writing Security Tools and Exploits 1, Foster, James C, eBook

PDF) Writing Security Tools and Exploits | asd qwe - Academia.edu

Network Security Tools: Writing, Hacking, and Modifying Security Tools

What Is an Exploit? - Cisco

Writing Security Tools and Exploits 1, Foster, James C, eBook

Penetration Tester Job Role, Skills, and Salary
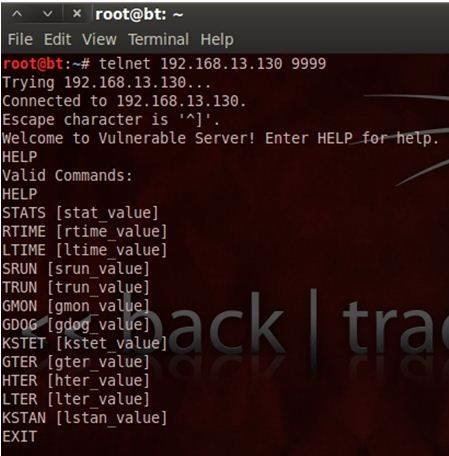
Exploit writing tutorial: Part 1 | Computer Weekly
Vulnerabilities and Exploits — ENISA

Writing Security Tools and Exploits 1, Foster, James C, eBook

Writing Security Tools and Exploits by James C Foster
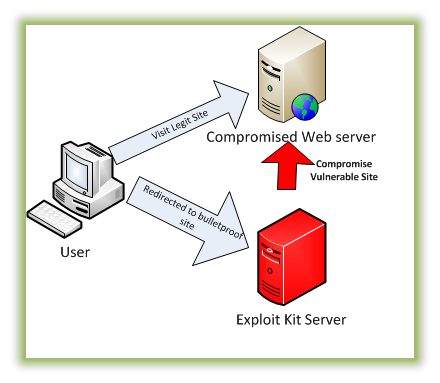
Tools of the Trade: Exploit Kits | Malwarebytes Labs

Today's most common security vulnerabilities explained - The

5 Best Programming Languages for Hacking in 2024 | Simplilearn
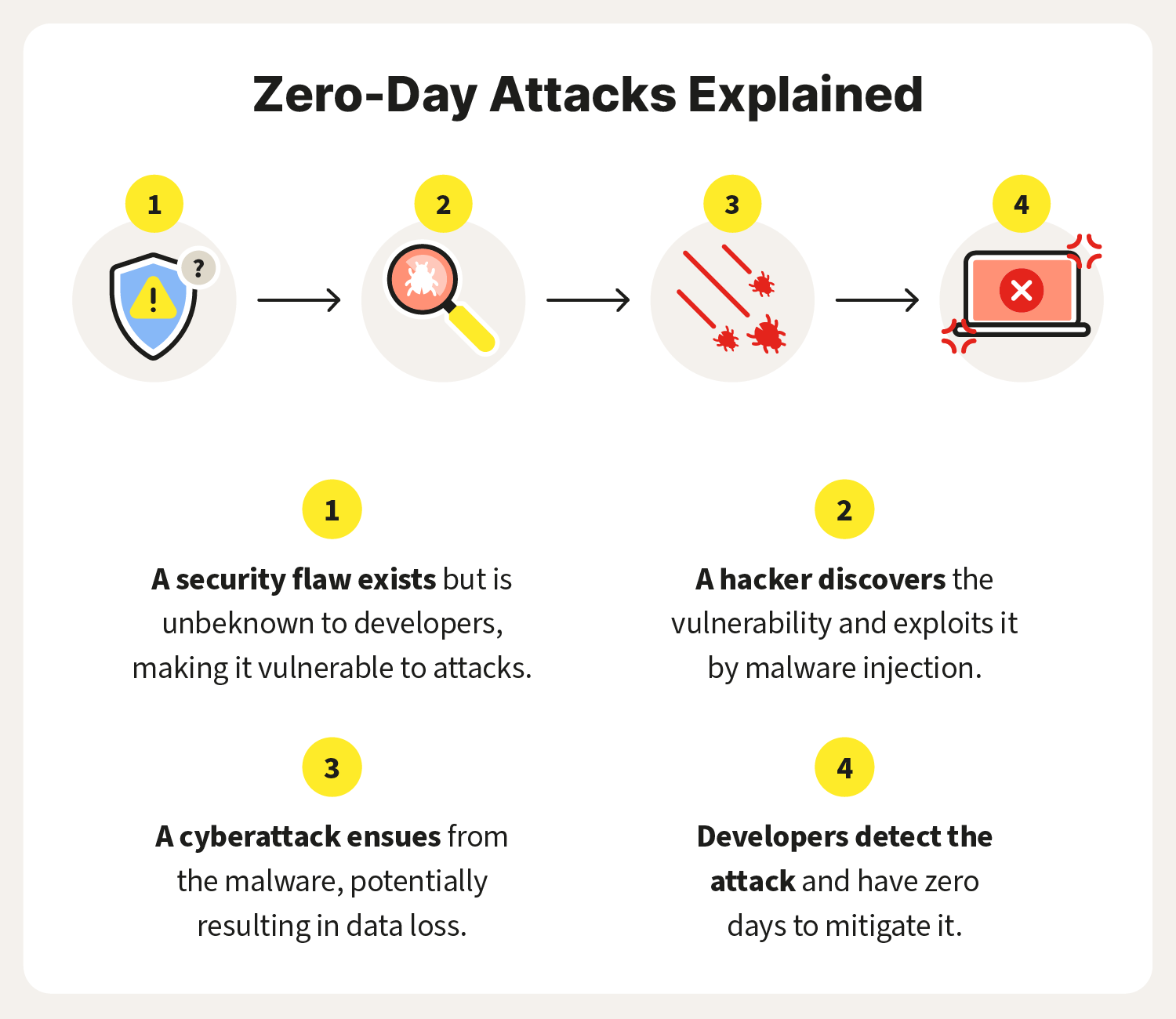
What is a zero-day exploit? Definition and prevention tips – Norton
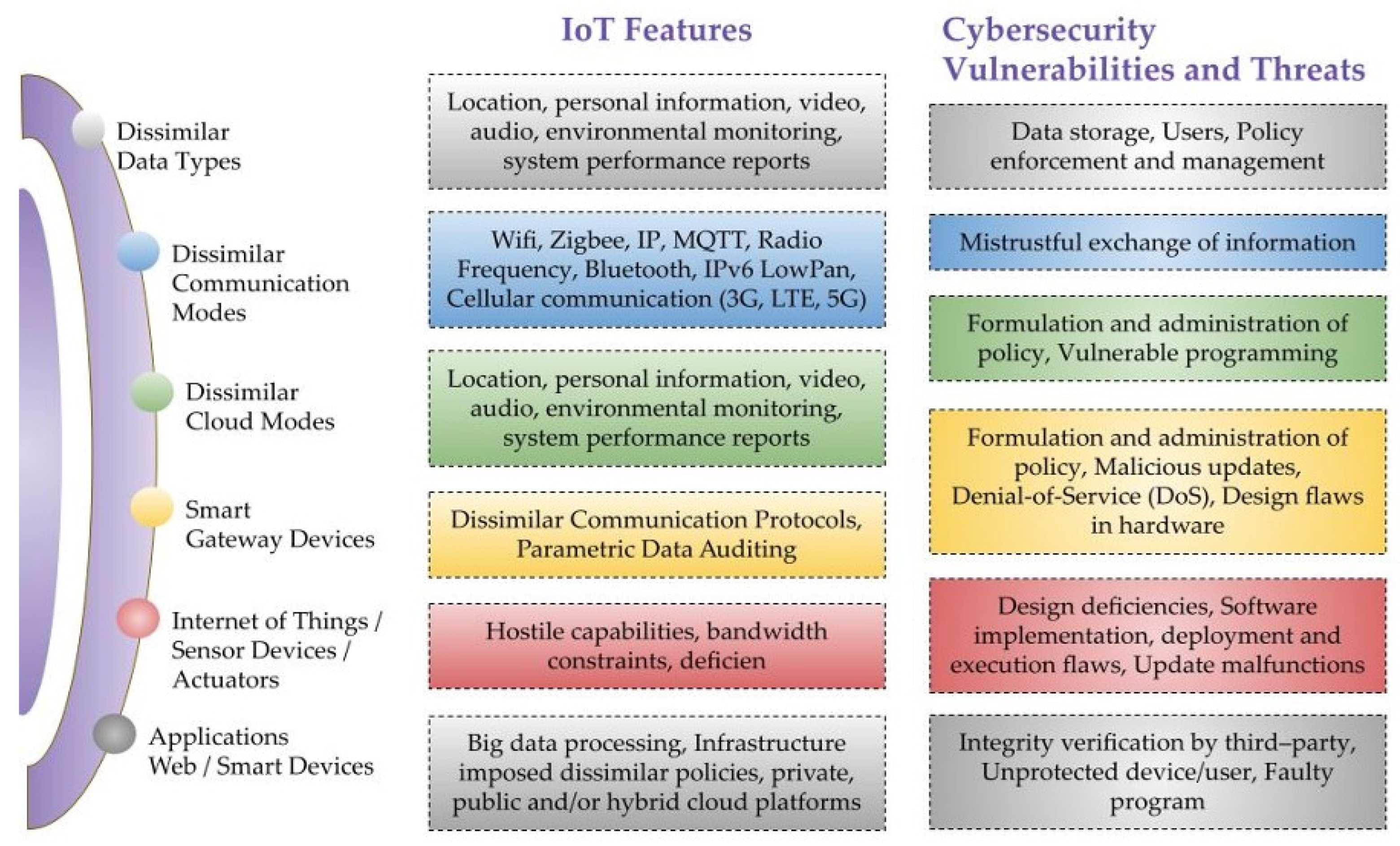
Sensors | Free Full-Text | A Critical Cybersecurity Analysis and

Exploit development resources - KaliTut

7 of the best programming languages for cybersecurity (offensive

What is a Software Vulnerability? | JFrog
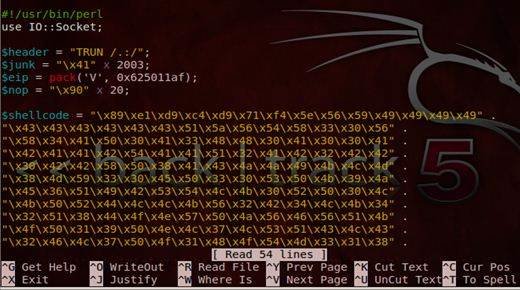
Exploit writing tutorial: Part 1 | Computer Weekly

Top 12 Open Source Code Security Tools - Spectral

Penetration Tester Job Role, Skills, and Salary

Best Open Source Security Testing Tools | QAwerk

Zero-Day Exploits: Definition & How It Works (With Examples)

PDF) Writing Security Tools and Exploits | asd qwe - Academia.edu
Hacking with ChatGPT: Five A.I. Based Attacks for Offensive Security

Top 25 Linux Security Tools to Boost Cyber Defense

Exploit writing tutorial: Part 1 | Computer Weekly

Using ChatGPT to write nuclei exploits | by Grzegorz Piechnik | Medium
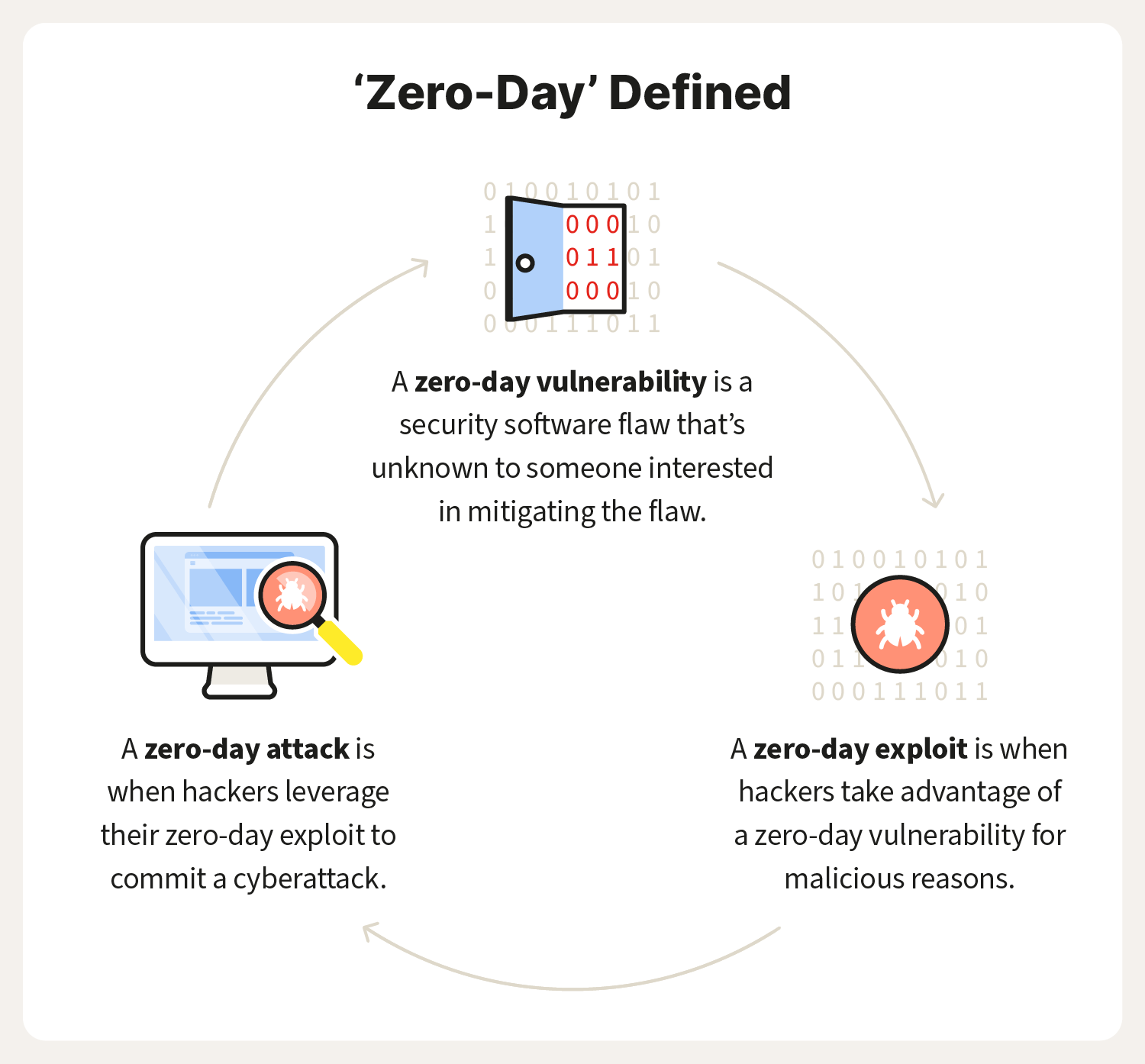
What is a zero-day exploit? Definition and prevention tips – Norton

Exploit Development: The Most Important Skill A Hacker Can Learn

Exploit the Fuzz – Exploiting Vulnerabilities in 5G Core Networks
Top 5 Vulnerability Management Tools


商品の情報
メルカリ安心への取り組み
お金は事務局に支払われ、評価後に振り込まれます
出品者
スピード発送
この出品者は平均24時間以内に発送しています














